Using Faketime for Ad-Hoc Kerberos Authentication
Installing Faketime
sudo apt install faketimefaketime -hThis will run the specified 'program' with the given 'arguments'.
The program will be tricked into seeing the given 'timestamp' as its starting date and time.
The clock will continue to run from this timestamp. Please see the manpage (man faketime)
for advanced options, such as stopping the wall clock and make it run faster or slower.
Example Usage
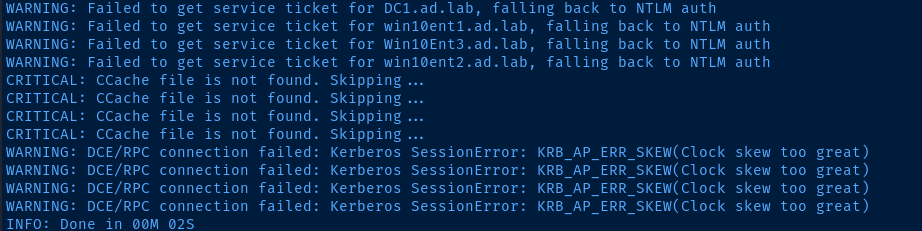
Running bloodhound-python in my local lab, the KDC on the target domain controller throws a clock skew error. So, we'll use ntpdate to synchronize with the KDC and feed that to faketime and then make the connection.
Before
bloodhound-python -c All -u joan.hesther -p 'madison' -d ad.lab -dc dc1.ad.lab -ns 10.80.80.2KRB_AP_ERR_SKEW(Clock skew too great) indicates the Kerberos client (Kali in this case) have to wide a drift between their clocks. To resolve, we can run an ad-hoc ntpdate sync and feed that to faketime to spoof the clock to bloodhound-python (or whichever Kerberos-authenticated app you're using).
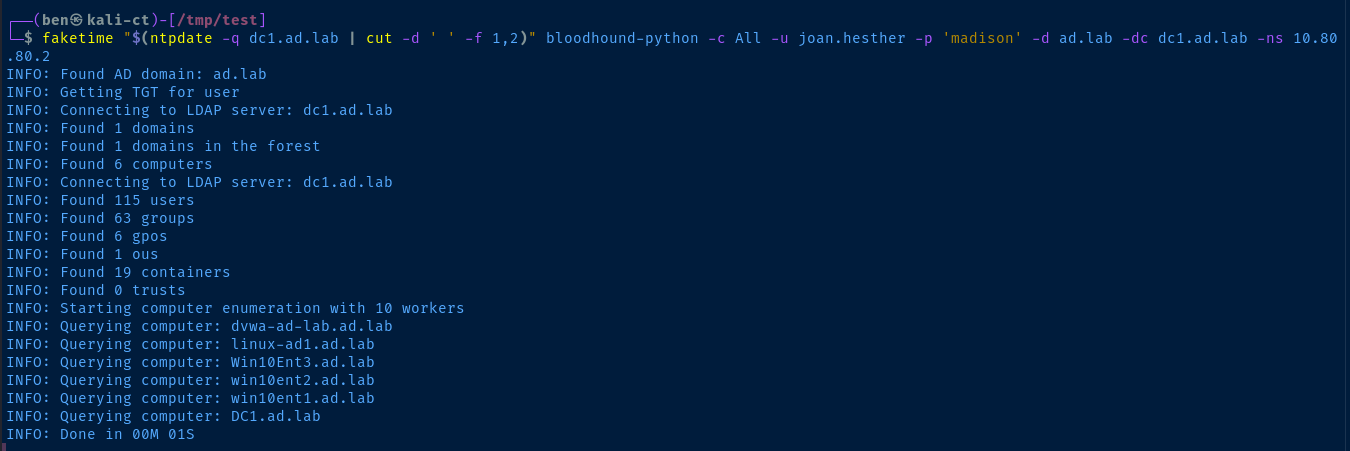
After
faketime "$(ntpdate -q dc1.ad.lab | cut -d ' ' -f 1,2)" bloodhound-python -c All -u joan.hesther -p 'madison' -d ad.lab -dc dc1.ad.lab -ns 10.80.80.2