Extracting Kerberos AS-REQ Pre-Auth Hashes from PCAPs
PCAP Analysis
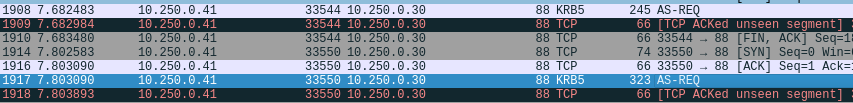
Note the existence of KRB5 protocol traffic on tcp/88, which is further identified as AS-REQ data. If we inspect the application layer data in the packets, we can see details such as username, domain info, etc. We should be able to carve this data out of the packet.
Using NetworkMiner on Kali
# Install mono as this is a Windows binary
sudo apt install -y mono-devel
# Download the latest free version
wget https://www.netresec.com/?download=NetworkMiner -O ./nm.zip
unzip nm.zip
mono NetworkMiner_2-8-1/NetworkMiner.exe --noupdatecheckOnce the program is launched, open the PCAP file.
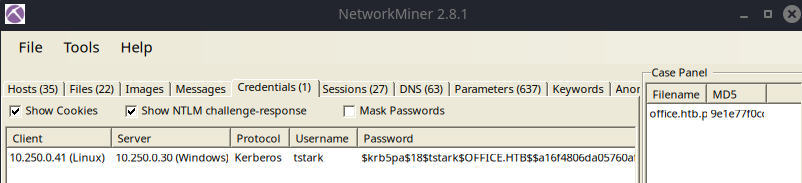
Right-click the password hash and choose copy password. Paste the contents into a file and crack with hashcat or john.
nano krb_hash
john --wordlist=rockyou.txt krb_hashReferences
Extracting Kerberos Credentials from PCAP (netresec.com)